To fully grasp the significance of January 6th and understand the orchestrated chaos that unfolded, it’s essential to examine the directives, national policies, executive orders, strategies, and doctrines related to intelligence. By understanding these processes, we can begin to identify the overreach and neglect that took place. I can assure you, however, that this was not the doing of Trump supporters.
Presidential Directives, National Policies, Executive Orders, National Strategies and Doctrines Related to Intelligence.
Presidential directives and national policies aren’t just paperwork—they’re the playbooks for how our government responds to threats. Without understanding these frameworks, it’s impossible to track whether they’re being followed or where failures occur. Corruption, inefficiency, or neglect hides in the gap between directives and execution. So, let’s break it down in a way that connects directly to domestic intelligence operations.
Presidential Directives and National Policies
Presidential directives, executive orders, and national strategies define how intelligence is gathered, processed, and disseminated within the U.S. These documents don’t just sit on shelves; they give agencies like the FBI, DHS, and others their marching orders for how to act on threats. Below are key examples and their relevance.
Presidential Policy Directives (PPDs)
PPDs are orders issued by the President that outline national security priorities and assign roles to federal agencies.
PPD-41: Cyber Incident Coordination
Issued in 2016, PPD-41 establishes how the federal government responds to significant cyber incidents, which are increasingly relevant to domestic threats.
FBI: Leads threat response, focusing on identifying perpetrators and neutralizing ongoing threats.
DHS (via CISA): Manages infrastructure protection and mitigates vulnerabilities.
ODNI: Coordinates the intelligence community’s analysis of cyber threats.
The directive emphasizes real-time information sharing among federal, state, and private-sector partners.
PPD-8: National Preparedness
PPD-8 focuses on preparing the nation for domestic emergencies, including natural disasters, pandemics, and terrorism. It requires agencies to integrate intelligence into preparedness efforts to ensure early detection of threats like domestic terrorism. This directive introduced the National Preparedness Goal, aligning federal, state, and local agencies with shared objectives.
Executive Orders (EOs)
Overview
EOs are legally binding orders from the President that direct federal agencies’ operations. While broader than PPDs, some EOs directly affect domestic intelligence.
EO 12333: United States Intelligence Activities
Issued in 1981, this EO governs the intelligence community’s operations, including the FBI’s role in domestic intelligence. It establishes strict compliance with privacy protections and authorizes the FBI to collect intelligence on foreign agents and domestic threats, provided it adheres to legal standards.
EO 13773: Enforcing Federal Law with Respect to Transnational Criminal Organizations
Issued in 2017, this EO prioritizes intelligence operations targeting criminal organizations that threaten domestic security. It enhances coordination between federal law enforcement and intelligence agencies to combat drug trafficking, human trafficking, and gang violence.
National Strategies and Doctrines
Overview
National strategies and doctrines provide high-level frameworks for addressing threats. While less specific than directives or orders, they shape the priorities and objectives of federal agencies.
National Security Strategy (NSS)
A presidentially-mandated document outlining the U.S. government’s top national security priorities, updated every few years to reflect emerging threats such as domestic terrorism and cyberattacks. Recent versions emphasize threats like white supremacist violence and critical infrastructure vulnerabilities.
National Defense Strategy (NDS)
Produced by the Department of Defense, the NDS outlines military priorities, including homeland defense. While focused on external threats, it addresses domestic terrorism through coordination with agencies like the FBI.
National Counterterrorism Strategy
This strategy focuses on preventing and disrupting terrorism, increasingly emphasizing domestic threats. It designates the FBI as the lead agency for counterterrorism investigations and promotes collaboration with state and local agencies through Joint Terrorism Task Forces (JTTFs).
Why This Matters
These directives, policies, and strategies represent the blueprints for how intelligence should be gathered, shared, and acted upon within the U.S. But as we’ve seen time and again, the gap between policy and practice is where failures thrive. Knowing these frameworks helps us identify where those failures occur—whether it’s in poor coordination, lack of urgency, or outright neglect.
Operational Frameworks
Now let’s talk about operational frameworks—the systems that turn laws, policies, and strategies into action. These frameworks are where the rubber meets the road. If the policies and strategies are the “what,” these frameworks are the “how.” They dictate how agencies like the FBI, DHS, and local law enforcement coordinate their efforts to handle intelligence, respond to threats, and manage crises.
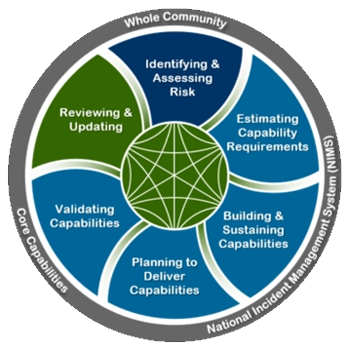
National Incident Management System (NIMS)
The National Incident Management System (NIMS), established by the Department of Homeland Security (DHS), provides a standardized approach to managing emergencies. This framework is critical for addressing intelligence-driven threats such as terrorism or domestic extremism, ensuring that federal, state, and local agencies can collaborate effectively during incidents.
At its core, NIMS incorporates the Incident Command System (ICS), a hierarchical chain-of-command structure that organizes response efforts to complex threats or emergencies. Intelligence gathered before or during an incident is funneled into the ICS, enabling coordinated decision-making and resource allocation. For example, during a suspected terrorist attack, the FBI might lead intelligence operations, but the deployment of resources and tactical responses would follow NIMS protocols to ensure efficiency and cohesion.
Despite its intentions, NIMS often falters due to weak links in real-time intelligence sharing. A glaring example of this was the January 6th Capitol attack, where poor dissemination of threat intelligence left multiple agencies unclear about security risks. This failure exposed systemic issues in how intelligence is integrated into NIMS operations.
Joint Terrorism Task Forces (JTTFs)
Joint Terrorism Task Forces (JTTFs), led by the FBI, serve as the operational backbone for counterterrorism efforts across the United States. Operating in cities nationwide, JTTFs bring together federal, state, and local law enforcement to close intelligence gaps and respond to domestic threats.
JTTFs emphasize prevention, working to identify and neutralize threats before they materialize. This collaborative approach leverages the strengths of participating agencies: the FBI provides technical surveillance capabilities, while local police contribute on-the-ground intelligence about their communities. By pooling resources, JTTFs aim to reduce silos and ensure that intelligence is shared and acted upon collectively.
However, the effectiveness of JTTFs is often undermined by uneven participation from local agencies and lapses in intelligence sharing. Historical failures, such as those preceding 9/11, highlighted significant gaps between FBI-led JTTFs and local law enforcement. These weaknesses persist, revealing systemic flaws in coordination and collaboration that compromise their mission to protect against terrorism and other threats.
Now let’s turn to coordination frameworks—the mechanisms that ensure intelligence and resources are shared and deployed across agencies effectively. These frameworks are where policies and operational responsibilities converge. If they work as intended, coordination frameworks prevent silos and ensure a seamless response to threats. When they fail, they create gaps that can lead to catastrophic breakdowns.
Coordination Frameworks
Intelligence Sharing: Fusion Centers
Fusion Centers were established as state-level intelligence hubs to address one of the most glaring failures of the post-9/11 era—the lack of real-time communication between intelligence agencies and law enforcement. These centers, operated by state or local governments with federal support, integrate data from federal agencies like the FBI and DHS, as well as state law enforcement and local police. By combining this information, they aim to create a comprehensive regional threat picture. Intelligence processed by Fusion Centers includes suspicious activity reports, social media monitoring, and regional threat assessments.
The importance of Fusion Centers lies in their role as a bridge between local law enforcement and federal agencies. For instance, if the FBI uncovers a credible domestic terrorism threat, the Fusion Center can disseminate that information to local police, who are best positioned to act. Despite their potential, critics argue that Fusion Centers often lack proper oversight and focus, leading to wasted resources on irrelevant or inaccurate intelligence. The January 6th Capitol attack highlighted persistent coordination failures, demonstrating that the promise of seamless communication remains unfulfilled.
Interagency Threat Coordination: National Counterterrorism Center (NCTC)
The National Counterterrorism Center (NCTC) was created under the Intelligence Reform and Terrorism Prevention Act of 2004 to serve as the primary hub for coordinating terrorism-related intelligence across federal agencies. Integrating inputs from 17 intelligence agencies, including the FBI, CIA, and DHS, the NCTC processes threat reports and produces comprehensive analyses. For example, if the FBI identifies a potential domestic terror cell, the NCTC ensures that relevant agencies like DHS have access to that intelligence.
The value of the NCTC lies in preventing duplication of effort and ensuring that all agencies work from the same threat picture. This coordination is particularly critical during high-profile events like major political gatherings or public celebrations. However, the effectiveness of the NCTC is often undermined by jurisdictional turf wars and privacy concerns, which can lead to withholding of information and diminished operational cohesion.
Incident Response: National Response Framework (NRF)
The National Response Framework (NRF), created by DHS, provides a unified structure for responding to national emergencies, including those driven by intelligence-related threats like terrorism or cyberattacks. The NRF clearly delineates roles for federal, state, and local entities during emergencies and includes specific annexes addressing incidents involving biological threats, terrorism, and critical infrastructure.
The framework’s importance lies in its ability to reduce confusion and duplication during a crisis. For example, in a coordinated terrorist attack, the FBI would typically lead the investigation, while DHS oversees public safety and FEMA manages disaster response. However, resource limitations and poor communication between agencies often hamper the NRF’s execution. These challenges were evident on January 6th, when the lack of coordination exacerbated the response delays.
Incident Command System (ICS)
The Incident Command System (ICS) is a standardized, scalable approach to incident management used across all levels of government. It establishes a clear chain of command and organizes response efforts into distinct sections such as operations, logistics, and planning. By doing so, ICS streamlines coordination and ensures that everyone involved understands their roles and responsibilities.
In practice, ICS prevents chaos during emergencies by centralizing decision-making. For example, in a domestic terrorism event, ICS could unify FBI-led intelligence operations with the tactical response of local law enforcement. However, the effectiveness of ICS depends on proper training and implementation, which varies widely across jurisdictions. This variability often leads to confusion, as was evident during January 6th, when fragmented leadership hindered the response.
Cyber Incident Coordination: CISA and FBI Cyber Division
The Cybersecurity and Infrastructure Security Agency (CISA), part of DHS, plays a central role in protecting critical infrastructure from cyber threats. It provides threat assessments and shares cyber intelligence with both public and private sectors. For example, if CISA identifies a ransomware attack targeting a power grid, it coordinates with utility companies, local law enforcement, and the FBI to mitigate the threat. However, CISA’s effectiveness is frequently hampered by resource constraints and its reliance on voluntary cooperation from private companies.
The FBI’s Cyber Division complements CISA’s efforts by investigating cybercrimes, ranging from ransomware attacks to espionage. The division collaborates with CISA and international law enforcement partners to identify and prosecute cybercriminals. While CISA focuses on infrastructure resilience, the FBI targets the perpetrators of cyberattacks, ensuring that actionable intelligence is shared with state and local partners. Despite these efforts, coordination with private companies remains a challenge, as businesses often hesitate to report breaches due to fears of reputational damage.
Coordination frameworks like Fusion Centers, the NCTC, the NRF, ICS, and cyber coordination mechanisms are critical to addressing modern threats. However, their effectiveness is consistently undermined by systemic issues, including poor communication, jurisdictional disputes, and resource constraints. To fulfill their intended purpose, these frameworks must overcome these challenges and adopt a more unified, transparent approach to intelligence sharing and incident response.
Why Coordination Frameworks Matter
These frameworks are the gears of the intelligence machine. They ensure that information isn’t just collected—it’s shared, acted upon, and integrated into broader response efforts. However, as history shows, when these frameworks break down, the result is often confusion, duplication of effort, or missed opportunities to prevent disaster.
Agency Roles and Responsibilities
Agencies play specific roles in the intelligence ecosystem, operating under laws and policies that define their mandates. Their responsibilities are divided based on expertise and jurisdiction. Below is an analysis of key agencies and how they fit into the framework of domestic intelligence.
Federal Bureau of Investigation (FBI)
The FBI serves as the lead federal agency for domestic counterterrorism, counterintelligence, and cybercrime. It oversees Joint Terrorism Task Forces (JTTFs), positioning itself as the primary point of contact for intelligence operations related to domestic threats.
The FBI’s key responsibilities include intelligence gathering through field offices, informants, and surveillance programs. The agency converts raw intelligence into actionable threat assessments and disseminates this information to other agencies such as DHS and local law enforcement. Beyond intelligence, the FBI enforces federal law by investigating and arresting individuals involved in domestic terrorism or espionage.
Department of Homeland Security (DHS)
DHS focuses on protecting critical infrastructure and coordinating responses to domestic threats, including natural disasters, terrorism, and cyberattacks. Its Office of Intelligence and Analysis (I&A) plays a central role in collecting and disseminating intelligence on domestic threats.
DHS’s responsibilities include safeguarding essential systems like power grids and financial networks under its critical infrastructure protection efforts. The department also operates Fusion Centers, regional intelligence hubs designed to share information between federal, state, and local agencies. Additionally, through the Cybersecurity and Infrastructure Security Agency (CISA), DHS defends against cyber threats.
Central Intelligence Agency (CIA)
The CIA’s role is centered on foreign intelligence, with legal prohibitions against domestic operations. However, the agency shares relevant intelligence with domestic entities when foreign threats intersect with U.S. borders.
The CIA provides insights into international threats that may spill over into domestic spaces, such as foreign-sponsored terrorism. It also collaborates with the FBI on cases where foreign intelligence has domestic implications. Despite its critical role in these scenarios, the CIA’s limited involvement in domestic intelligence—as mandated by law—can slow coordination in cross-border cases.
National Security Agency (NSA)
The NSA is responsible for collecting signals intelligence (SIGINT), including communications intercepted within the U.S., under strict legal oversight. It supports agencies like the FBI and DHS by providing technical intelligence.
The NSA’s cybersecurity efforts focus on monitoring foreign cyber threats targeting domestic infrastructure. It also assists the FBI in monitoring communications of domestic actors linked to foreign threats, often under the provisions of the Foreign Intelligence Surveillance Act (FISA). However, the NSA’s bulk data collection programs, such as those revealed by Edward Snowden, have sparked significant privacy and overreach concerns, complicating its relationship with the public.
Local and State Law Enforcement
State and local agencies serve as the first line of defense against domestic threats, particularly in areas where federal presence is limited. These agencies provide on-the-ground intelligence about local threats and coordinate with federal entities through Fusion Centers and JTTFs.
Despite their critical role, local and state law enforcement often face resource constraints that hinder their capacity to respond effectively. Inconsistent collaboration with federal agencies can further limit their impact on intelligence operations, creating gaps in the overall security framework.
Why This Matters
The operational frameworks and agency roles we’ve discussed are meant to ensure that intelligence is effectively gathered, shared, and acted upon. But as history shows, breakdowns often occur at the intersections—when frameworks don’t align, or when agencies fail to communicate.
The devil is always in the details, and understanding these roles and systems is crucial to pinpointing exactly where accountability is needed. Every safeguard—from the Constitution itself, to federal statutes, to the FBI’s internal policies and operational frameworks—was designed to prevent abuse of power and ensure the fair and just application of the law.
Now ask yourself this: do you truly believe that violating every single level of oversight, every safeguard that we’ve discussed in the past two articles, was purely accidental? Was it just a matter of incompetence, or was it something far more deliberate—an intentional disregard for the principles that are supposed to guide and restrain the most powerful law enforcement agency in the country?
Accountability isn’t just about acknowledging failures; it’s about understanding whether those failures were systemic, intentional, or the result of negligence. Without this understanding, we risk perpetuating a system where laws and policies are nothing more than words on paper, ignored by those who are supposed to uphold them. This is the question that lies at the heart of these articles, and it’s one we cannot afford to leave unanswered.
With this understanding, let’s dive into the staggering violations that unfolded on January 6th—violations born from inaction, systemic failures, and the political bias that we all witnessed in real time.










THANK YOU
‘But as we’ve seen time and again, the gap between policy and practice is where failures thrive.’ Or, where the insidious plans to infiltrate and pervert the original mandate. It seems plausible that we have too many federal-level entities that are not mandated or under the authority of the Constitution. I worked several major hurricane responses and recoveries with FEMA, Region IV (Atlanta) and the coordination between state, local, other state compacts with IV was good. But, we had planned and pre-coordinated operations and roles together. The first time we had an issue….when someone was sent from DC FEMA.
The descriptions you’ve provided are exactly how we were told these agencies’ roles and responsibilities were. Infiltration (planned) changed this over time, expanding roles, controls, etc., all hidden from the public. The school shootings and the other incidents (with hindsight) reveal how well the infiltration worked. We must mandate a complete review of all federal agencies in accordance with the federal level of responsibility stated in the Constitution. Why do we need 17-19 federal intelligence operations in the various bureaucracies?
Wonderful information and a map to restore limited authority at the federal level. I’m saving this series for future reference.