The DISARM Foundation: What Do You Know About It?
How many of you have heard of the DISARM Foundation? This foundation provides an open-source master framework designed to combat disinformation through the sharing of data, analysis, and the coordination of effective actions. This powerful framework is available worldwide and is utilized by prominent institutions, including the European Union, the United Nations, and NATO. It’s also employed by government teams in countries like the U.S. and Canada, as well as by a number of specific project teams. But who exactly are these specific project teams? That’s something worth investigating.
DISARM claims that its framework has been instrumental in establishing new institutions, such as Cognitive Security, the Computer Incident Response Center in Luxembourg, and the Open Factos analysis program. It’s been used to train journalists in Kenya and Nigeria and has even been employed by the World Health Organization to counter anti-vaccine campaigns across Europe. Let that sink in.
In short, the DISARM Foundation offers a tool—a weapon, really—that can be used by anyone, against anyone. We need to understand what this framework is and how it can be wielded, because since being exposed to it, thanks to Bear Crawl, I’ve been shocked by its potential impact.
As we explore this further, I urge you to consider the role of political action committees, Super PACs, political advocacy groups, and entities like Democracy Alliance. Understanding DISARM is crucial because this structured framework has the potential to cause significant harm to the American people.
How Does DISARM Work?
A few of us have shared this information with many others, but surprisingly, it hasn't been taken seriously. I'm here to tell you that this system and framework is being used every day. I strongly urge you to visit the website through the link I've provided and see for yourself. Explore the content, because within these frameworks are tactics and techniques that can reveal a lot about what's happening in this era of fifth-generation warfare. Let's dive into what the DISARM Framework really is.
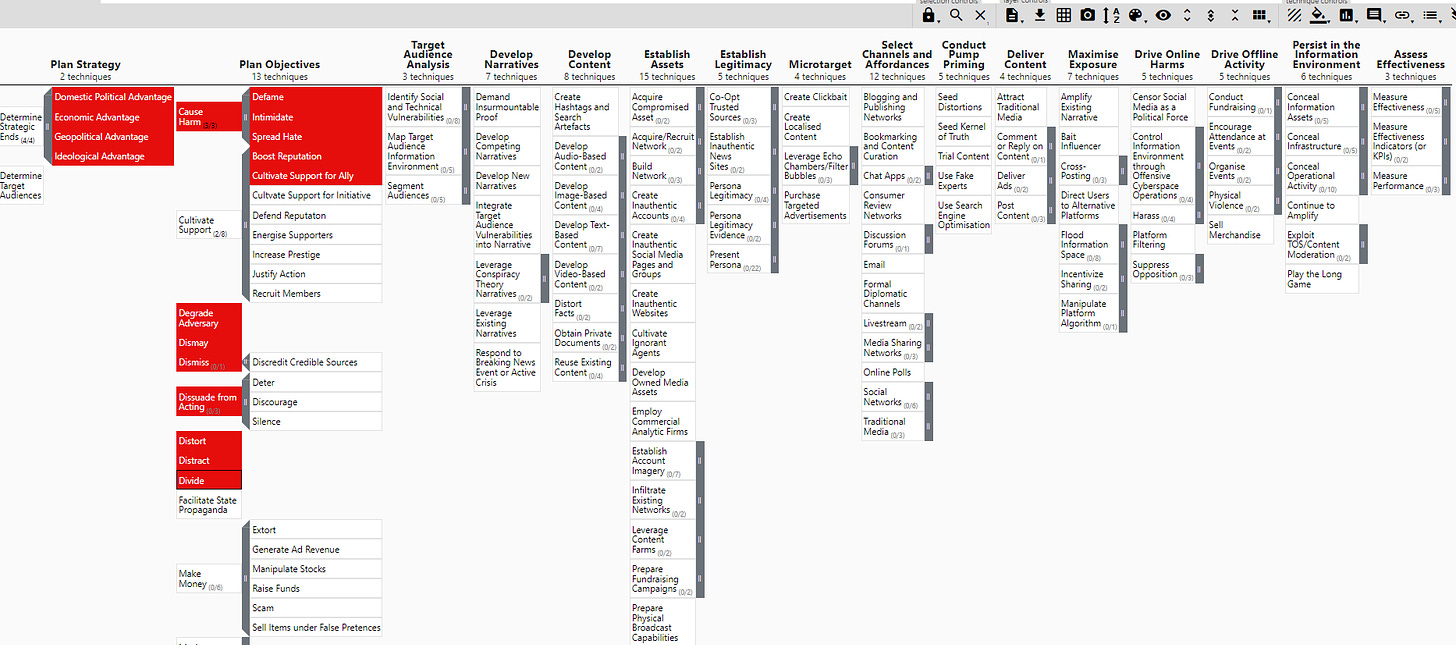
DISARM Framework Explorer
The DISARM Framework Explorer provides a systematic breakdown of how disinformation incidents occur, how they are detected, and how they are countered. While this can be a valuable tool for defending against disinformation, it's crucial to recognize that it can also be weaponized—and I believe it has been. When you click on the link above, you'll encounter various DISARM Objects. (You’ll want to click on all the links indicated by underlined words). These include Frameworks,
Phases - A phase is the highest-level grouping of tactics and their associated techniques, corresponding to a logical stage in the execution of an influence campaign. The phases are,
P01: Plan - Envision the desired outcome. Lay out effective ways of achieving it.
P02: Prepare - Activities conducted before execution to improve the ability to conduct the action.
P03: Execute - Run the action, from initial exposure to wrap-up and/or maintaining presence.
P04: Assess - Evaluate effectiveness of action, for use in future plans.
Tactics - A tactic is a way or means by which the objectives (ends) are met, and which does not prescribe either the specific techniques or procedures used to achieve it.
Techniques - Techniques are the “how” of a particular tactic. Techniques are associated with one or more tactics, as a particular technique may be used to accomplish different goals.
Tasks - A task is essentially the detailed, practical step or steps that operationalize a technique to accomplish a tactic’s objective.
Countermeasures - Are actions taken to defend against or reduce the impact of a disinformation incident. Within the context of the DISARM Blue framework, countermeasures are the specific steps that a response team or organization might take to protect people from being misled, slow down the spread of false information, or stop it altogether. Think of countermeasures as the defensive moves you make to keep a bad situation from getting worse.
Detections - Refer to the methods or tools used to identify and recognize the presence of a disinformation incident. These are the ways in which a response team can spot signs of false information being spread, whether it's through monitoring social media, analyzing suspicious patterns in data, or using specialized software to track the spread of misleading content.
Response Types - These are the various ways a response team can react to disinformation, depending on the situation. There are seven types,
D01 Detect: Discover or discern the existence, presence, or fact of an intrusion into information systems.
D02 Deny: Prevent disinformation creators from accessing and using critical information, systems, and services. Deny is for an indefinite time period.
D03 Disrupt: Completely break or interrupt the flow of information, for a fixed amount of time. (Deny, for a limited time period). Not allowing any efficacy, for a short amount of time.
D04 Degrade: Reduce the effectiveness or efficiency of disinformation creators’ command and control or communications systems, and information collection efforts or means, either indefinitely, or for a limited time period.
D05 Deceive: Cause a person to believe what is not true. military deception seeks to mislead adversary decision makers by manipulating their perception of reality.
D06 Destroy: Damage a system or entity so badly that it cannot perform any function or be restored to a usable condition without being entirely rebuilt. Destroy is permanent, e.g. you can rebuild a website, but it’s not the same website.
D07 Deter: Discourage.
Meta-Techniques - the "big-picture strategies" that help decide which specific techniques to use and how to combine them to achieve the best results in countering disinformation.
Playbooks - are comprehensive guides that outline a series of steps or actions to follow in specific scenarios when dealing with disinformation. They provide detailed instructions on how to respond to particular types of incidents, using the various tactics, techniques, and countermeasures available.
Resources - are like the "supplies and tools" you need to fight disinformation—everything that helps you do the job right, from information and technology to expert advice.
Additionally, under Data Objects, you'll find:
Incidents - Refer to specific occurrences or events where disinformation is being spread. These are the actual cases of false or misleading information being used to deceive or manipulate the public
Examples - Of prior incidents and their outcomes.
External Groups - Refer to organizations, teams, or entities outside of your immediate response team that may be involved in either spreading disinformation or helping to counter it. These could include social media platforms, government agencies, non-governmental organizations (NGOs), or even other countries. External groups can either be part of the problem, as in those who might be spreading disinformation, or part of the solution, as in those who collaborate to help detect and counter it. (Pay attention to this one, you’ll see what I mean in layer parts).
Tools - Refer to the software, applications, and technologies used to detect, analyze, counter, and respond to disinformation incidents. These can include monitoring tools that track the spread of disinformation, data analysis programs that help identify patterns, or platforms that facilitate communication and coordination among response teams.
DISARM Frameworks
Next, let's talk about the frameworks themselves. Currently, there are three frameworks:
DISARM Red: This is the incident creation framework. It outlines everything an incident creator needs to do to create, execute, and assess the effectiveness of a disinformation incident.
DISARM Blue: This is the incident counters framework. It covers all the steps a response team, as well as external people and organizations, must take to mitigate, slow down, or stop the effects of a disinformation incident.
DISARM Green: This is the counter-counters framework. It details the actions an incident creation team might take to undermine the effectiveness of mitigations, counters, and responses to an incident. Officially, this framework doesn’t exist yet—it’s marked as an idea for future work. However, as I browse their website, I can’t help but feel that DISARM Green might already exist, even if they haven’t posted it yet. But that’s just my opinion.
As you can see, there are highly organized structures in place for detecting disinformation and misinformation—and, in my opinion, these same structures can also be weaponized. I’ll leave it to you to form your own conclusions, but in the next part, we’re going to dive deeper. We’ll discuss some indicators of operations currently in play, using logic and discernment. I’ll see you in the next article—proceed to Part Three. See you there!
"Understanding the enemy’s playbook is the first step in turning the tide. Ignorance is not an option—because when you don’t know how the game is played, you’re already losing."